Preparation
Create OU for RDS Server in Active Directory. Create security group for users who will use Remote Desktop Host (i.e. RDS Users). Create GPO (i.e. RDS Server Lock Down). In Security Filtering delete Authenticated Users, add RDS Server Computer Account, and the security group created in previous step.
Configure users who can connect to the server remotely:
Log in to RDS Server >>> Run >>> control system >>> Remote Settings >>> Remote tab >>> Select users >>> Delete any groups/users >>> Add security group for RDS users
Disable Server Manager Pop Up at user log on:
On RDS Server open Task Scheduler. Navigate to Task Scheduler Library\Microsoft\Windows\Server Manager. Disable task “ServerManager” which triggers at log on of any user.
Some group policies might not be available in your group policy manager. You will need to add Administrative Templates for the Windows 8.1 and Windows Server 2012 R2: see Adding Windows 8.1 and Server 2012 R2 Administrative Templates.
Configure Group Policy for RDS Server Lock Down
Loopback Processing
[Computer Configuration\Policies\Administrative Templates\System\Group Policy]
Configure user Group Policy loopback processing mode: Enable – Merge
This policy setting directs the system to apply the set of Group Policy objects for the computer to any user who logs on to a computer affected by this setting. It is intended for special-use computers, such as those in public places, laboratories, and classrooms, where you must modify the user setting based on the computer that is being used.
If you enable this setting, you can select one of the following modes from the Mode box:
“Replace” indicates that the user settings defined in the computer’s Group Policy Objects replace the user settings normally applied to the user.
“Merge” indicates that the user settings defined in the computer’s Group Policy Objects and the user settings normally applied to the user are combined. If the settings conflict, the user settings in the computer’s Group Policy Objects take precedence over the user’s normal settings.
Disable Control Panel Items
[User Configuration\Policies\Administrative Templates\Control Panel]
Hide specified Control Panel items: Enable
This setting allows you to display or hide specified Control Panel items, such as Mouse, System, or Personalization, from the Control Panel window and the Start screen. The setting affects the Start screen and Control Panel window, as well as other ways to access Control Panel items, such as shortcuts in Help and Support or command lines that use control.exe. This policy has no effect on items displayed in PC settings.
If you enable this setting, you can select specific items not to display on the Control Panel window and the Start screen.
To hide a Control Panel item, enable this policy setting and click Show to access the list of disallowed Control Panel items. In the Show Contents dialog box in the Value column, enter the Control Panel item’s canonical name. For example, enter Microsoft.Mouse, Microsoft.System, or Microsoft.Personalization.
Add following items to the disallowed Control Panel items:
Microsoft.AdministrativeTools
Microsoft.AutoPlay
Microsoft.ActionCenter
Microsoft.ColorManagement
Microsoft.DefaultPrograms
Microsoft.DeviceManager
Microsoft.EaseOfAccessCenter
Microsoft.FolderOptions
Microsoft.iSCSIInitiator
Microsoft.NetworkAndSharingCenter
Microsoft.NotificationAreaIcons
Microsoft.PhoneAndModem
Microsoft.PowerOptions
Microsoft.ProgramsAndFeatures
Microsoft.System
Microsoft.TextToSpeech
Microsoft.UserAccounts
Microsoft.WindowsFirewall
Microsoft.WindowsUpdate
Microsoft.DateAndTime
Microsoft.RegionAndLanguage
Microsoft.RemoteAppAndDesktopConnections
Install Application On Remote Desktop Server
Java
Flash Player
Remove Administrative Tools and Powershell
Restrict access to Administrative tools
- Open RDS Lock Down Group Policy.
- Navigate to Computer Configuration >>> Policies >>> Windows Settings >>> Security Settings
- Right click on File System, choose Add File… .
- In the Add a file or folder window, put %AllUsersProfile%\Microsoft\Windows\Start Menu\Programs\Administrative Tools in the Folder field and click OK.

- On the next window Database Security for %AllUsersProfile%\Microsoft\Windows\Start Menu\Programs\Administrative Tools\Server Manager.lnk remove Users and check that Administrators have Full Access

- On the Add Object window choose Configure this file or folder then Propagate inheritable permissions to all subfolders and files. Click OK.
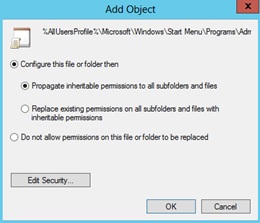
- Do the same for PowerShell shortcut (+ delete Creator Owner in database security): %AllUsersProfile%\Microsoft\Windows\Start Menu\Programs\System Tools\Windows PowerShell.lnk
- Do the same for Server Manager shortcut: %AllUsersProfile%\Microsoft\Windows\Start Menu\Programs\Administrative Tools\Server Manager.lnk
File Explorer Configuration
[User Configuration\Policies\Administrative Templates\Windows Components\File Explorer]
Enable – Restrict A, B, C and D drives only: Hide these specified drives in My Computer
This policy setting allows you to hide these specified drives in My Computer. This policy setting allows you to remove the icons representing selected hard drives from My Computer and File Explorer. Also, the drive letters representing the selected drives do not appear in the standard Open dialog box. If you enable this policy setting, select a drive or combination of drives in the drop-down list.
Enable – Remove Hardware tab
This setting removes the Hardware tab from Mouse, Keyboard, and Sounds and Audio Devices in Control Panel. It also removes the Hardware tab from the Properties dialog box for all local drives, including hard drives, floppy disk drives, and CD-ROM drives. As a result, users cannot use the Hardware tab to view or change the device list or device properties, or use the Troubleshoot button to resolve problems with the device.
Enable – Hides the Manage item on the File Explorer context menu
Removes the Manage item from the File Explorer context menu. This context menu appears when you right-click File Explorer or My Computer.
Enable – Remove Security tab
Removes the Security tab from File Explorer. If you enable this setting, users opening the Properties dialog box for all file system objects, including folders, files, shortcuts, and drives, will not be able to access the Security tab. As a result, users will be able to neither change the security settings nor view a list of all users that have access to the resource in question.
Disable Registry Modification
[User Configuration\Policies\Administrative Templates\System]
Enable – Prevent access to registry editing tools
Disables the Windows registry editor Regedit.exe. If you enable this policy setting and the user tries to start Regedit.exe, a message appears explaining that a policy setting prevents the action.
Configure Windows Installer and Windows Updates
[Computer Configuration\Policies\Administrative Templates\Windows Components\Windows Installer]
Enable: Prevent users from using Windows Installer to install updates and upgrades
This policy setting prevents users from using Windows Installer to install patches. If you enable this policy setting, users are prevented from using Windows Installer to install patches. Patches are updates or upgrades that replace only those program files that have changed. Because patches can be easy vehicles for malicious programs, some installations prohibit their use.
Enable Always: Turn off Windows Installer
This policy setting restricts the use of Windows Installer. If you enable this policy setting, you can prevent users from installing software on their systems or permit users to install only those programs offered by a system administrator. You can use the options in the Disable Windows Installer box to establish an installation setting.
[Computer Configuration\Administrative Templates\Windows Components\Windows Update]
Enable: Do not display ‘Install Updates and Shut Down’ option
This policy setting prevents users from using Windows Installer to install patches. If you enable this policy setting, users are prevented from using Windows Installer to install patches. Patches are updates or upgrades that replace only those program files that have changed. Because patches can be easy vehicles for malicious programs, some installations prohibit their use.
[Computer Configuration\Administrative Templates\Windows Components\Windows Update]
Enable: Do not display ‘Install Updates and Shut Down’ option
This policy setting allows you to manage whether the ‘Install Updates and Shut Down’ option is displayed in the Shut Down Windows dialog box.
Disable: Allow non-administrators to receive update notifications
This policy setting allows you to control whether non-administrative users will receive update notifications based on the “Configure Automatic Updates” policy setting.
Additional Policies
[Computer Configuration\Policies\Administrative Templates\Windows Components\Remote Desktop Services\Remote Desktop Session Host\Session Time Limits]
Enable (i.e. 30 minutes): Set time limit for disconnected sessions
You can use this policy setting to specify the maximum amount of time that a disconnected session remains active on the server. By default, Remote Desktop Services allows users to disconnect from a Remote Desktop Services session without logging off and ending the session.
When a session is in a disconnected state, running programs are kept active even though the user is no longer actively connected. By default, these disconnected sessions are maintained for an unlimited time on the server.
If you enable this policy setting, disconnected sessions are deleted from the server after the specified amount of time. To enforce the default behavior that disconnected sessions are maintained for an unlimited time, select Never. If you have a console session, disconnected session time limits do not apply.
[Computer Configuration/Policies/Administrative Templates/Windows Components/Remote Desktop Services/Remote Desktop Connection/Remote Desktop Session Host/Session Time Limits]
Set time limit for logoff of RemoteApp sessions: Enable (i.e. logoff delay 1 hour)
This policy setting allows you to specify how long a user’s RemoteApp session will remain in a disconnected state after closing all RemoteApp programs before the session is logged off from the RD Session Host server.
By default, if a user closes a RemoteApp program, the session is disconnected from the RD Session Host server, but it is not logged off.
If you enable this policy setting, when a user closes the last running RemoteApp program associated with a session, the RemoteApp session will remain in a disconnected state until the time limit that you specify is reached. When the time limit specified is reached, the RemoteApp session will be logged off from the RD Session Host server. If the user starts a RemoteApp program before the time limit is reached, the user will reconnect to the disconnected session on the RD Session Host server.
If you disable or do not configure this policy setting, when a user closes the last RemoteApp program, the session will be disconnected from the RD Session Host server but it is not logged off.
Note: This policy setting appears in both Computer Configuration and User Configuration. If both policy settings are configured, the Computer Configuration policy setting takes precedence.
[Computer Configuration/Policies/Administrative Templates/Windows Components/Remote Desktop Services/Remote Desktop Connection/Remote Desktop Session Host/Session Time Limits]
Set time limit for active but idle Remote Desktop Services sessions: Enable ( i.e. 1 hour)
This policy setting allows you to specify the maximum amount of time that an active Remote Desktop Services session can be idle (without user input) before it is automatically disconnected.
If you enable this policy setting, you must select the desired time limit in the Idle session limit list. Remote Desktop Services will automatically disconnect active but idle sessions after the specified amount of time. The user receives a warning two minutes before the session disconnects, which allows the user to press a key or move the mouse to keep the session active. If you have a console session, idle session time limits do not apply.
If you disable or do not configure this policy setting, the time limit is not specified at the Group Policy level. By default, Remote Desktop Services allows sessions to remain active but idle for an unlimited amount of time.
If you want Remote Desktop Services to end instead of disconnect a session when the time limit is reached, you can configure the policy setting Computer Configuration\Administrative Templates\Windows Components\Remote Desktop Services\Remote Desktop Session Host\Session Time Limits\End session when time limits are reached.
[User Configuration/Policies/Administrative Templates/Start Menu and Taskbar]
Go to the desktop instead of Start when signing in or when all the apps on a screen are closed: Enable
This policy setting allows users to go to the desktop instead of the Start screen when they sign in, or when all the apps on a screen are closed. This policy setting applies to all versions of Windows, and versions of Windows Server with the Desktop Experience installed.
If you enable this policy setting, users will always go to the desktop when they sign in, or when all the apps on a screen are closed.
[User Configuration/Policies/Administrative Templates/Start Menu and Taskbar]
Remove the Action Center icon: Enable
This policy setting allows you to remove the Action Center from the system control area.
If you enable this policy setting, the Action Center icon is not displayed in the system notification area.
If you disable or do not configure this policy setting, the Action Center icon is displayed in the system notification area.
[User Configuration/Policies/Administrative Templates/Windows Components/Windows Update]
Remove access to use all Windows Update features: Enable (0 = Do not show any notifications)
This setting allows you to remove access to Windows Update.
If you enable this setting, all Windows Update features are removed. This includes blocking access to the Windows Update Web site at http://windowsupdate.microsoft.com, from the Windows Update hyperlink on the Start menu, and also on the Tools menu in Internet Explorer. Windows automatic updating is also disabled; you will neither be notified about nor will you receive critical updates from Windows Update. This setting also prevents Device Manager from automatically installing driver updates from the Windows Update Web site.
If enabled you can configure one of the following notification options:
0 = Do not show any notifications
This setting will remove all access to Windows Update features and no notifications will be shown.
1 = Show restart required notifications
This setting will show notifications about restarts that are required to complete an installation.
[User Configuration/Policies/Administrative Templates/Windows Components/File Explorer]
Remove CD Burning features: Enable
This policy setting allows you to remove CD Burning features. File Explorer allows you to create and modify re-writable CDs if you have a CD writer connected to your PC.
If you enable this policy setting, all features in the File Explorer that allow you to use your CD writer are removed.
If you disable or do not configure this policy setting, users are able to use the File Explorer CD burning features.
Note: This policy setting does not prevent users from using third-party applications to create or modify CDs using a CD writer.
[User Configuration/Policies/Administrative Templates/Windows Components/File Explorer]
Prevent access to drives from My Computer: Enable (choose the drives)
Prevents users from using My Computer to gain access to the content of selected drives.
If you enable this setting, users can browse the directory structure of the selected drives in My Computer or File Explorer, but they cannot open folders and access the contents. Also, they cannot use the Run dialog box or the Map Network Drive dialog box to view the directories on these drives.
To use this setting, select a drive or combination of drives from the drop-down list. To allow access to all drive directories, disable this setting or select the “Do not restrict drives” option from the drop-down list.
Note: The icons representing the specified drives still appear in My Computer, but if users double-click the icons, a message appears explaining that a setting prevents the action.
Also, this setting does not prevent users from using programs to access local and network drives. And, it does not prevent them from using the Disk Management snap-in to view and change drive characteristics.
[User Configuration/Policies/Administrative Templates/Windows Components/Credentials User Interface]
Do not display the password reveal button: Enable
This policy setting allows you to configure the display of the password reveal button in password entry user experiences.
If you enable this policy setting, the password reveal button will not be displayed after a user types a password in the password entry text box.
If you disable or do not configure this policy setting, the password reveal button will be displayed after a user types a password in the password entry text box.
By default, the password reveal button is displayed after a user types a password in the password entry text box. To display the password, click the password reveal button.
The policy applies to all Windows components and applications that use the Windows system controls, including Internet Explorer.
[User Configuration/Policies/Administrative Templates/Windows Components/AutoPlay Policies]
Turn off Autoplay: Enable (CD-ROM and removable media drives)
This policy setting allows you to turn off the Autoplay feature.
Autoplay begins reading from a drive as soon as you insert media in the drive. As a result, the setup file of programs and the music on audio media start immediately.
Prior to Windows XP SP2, Autoplay is disabled by default on removable drives, such as the floppy disk drive (but not the CD-ROM drive), and on network drives.
Starting with Windows XP SP2, Autoplay is enabled for removable drives as well, including Zip drives and some USB mass storage devices.
If you enable this policy setting, Autoplay is disabled on CD-ROM and removable media drives, or disabled on all drives.
This policy setting disables Autoplay on additional types of drives. You cannot use this setting to enable Autoplay on drives on which it is disabled by default.
If you disable or do not configure this policy setting, AutoPlay is enabled.
Note: This policy setting appears in both the Computer Configuration and User Configuration folders. If the policy settings conflict, the policy setting in Computer Configuration takes precedence over the policy setting in User Configuration.
[User Configuration/Policies/Administrative Templates/Windows Components/Remote Desktop Services/Remote Desktop Connection]
Do not allow passwords to be saved: Enable
Controls whether a user can save passwords using Remote Desktop Connection.
If you enable this setting the credential saving checkbox in Remote Desktop Connection will be disabled and users will no longer be able to save passwords. When a user opens an RDP file using Remote Desktop Connection and saves his settings, any password that previously existed in the RDP file will be deleted.
If you disable this setting or leave it not configured, the user will be able to save passwords using Remote Desktop Connection




























































































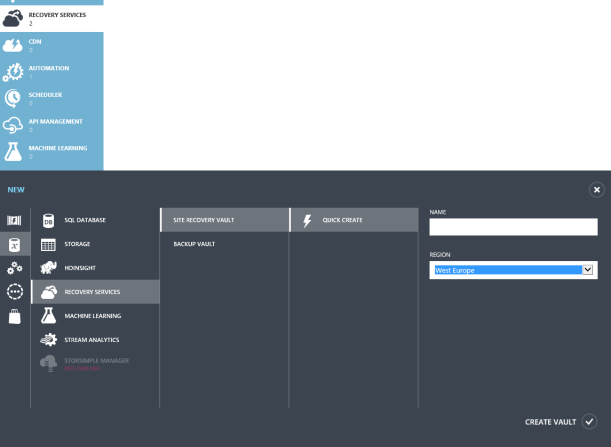
 – Select the storage account your VHD is in and click Open. This returns you to the Create an image from a VHD window. – After you return to the Create an image from a VHD window, select the Operating System Family. – Check I have run Sysprep on the virtual machine associated with this VHD to acknowledge that you generalized the operating system in Step 1, and then click OK.
– Select the storage account your VHD is in and click Open. This returns you to the Create an image from a VHD window. – After you return to the Create an image from a VHD window, select the Operating System Family. – Check I have run Sysprep on the virtual machine associated with this VHD to acknowledge that you generalized the operating system in Step 1, and then click OK.